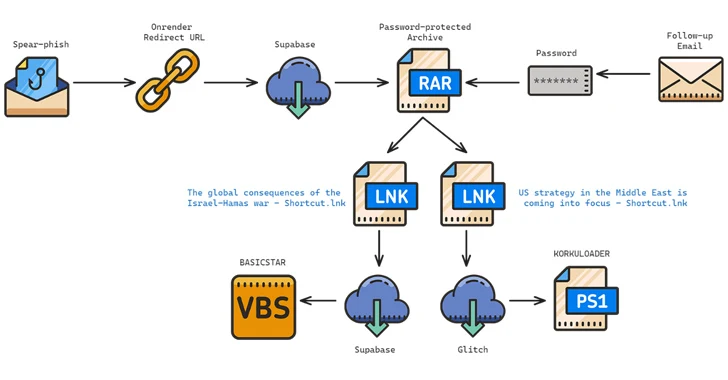
Iran and Hezbollah Hackers Launch Attacks to Influence Israel-Hamas Narrative
[ad_1] Hackers backed by Iran and Hezbollah staged cyber attacks designed to undercut public support for the Israel-Hamas war after October 2023. This includes destructive attacks against key Israeli organizations, hack-and-leak operations targeting entities in Israel and the U.S., phishing campaigns designed to steal intelligence, and information operations to turn public opinion against Israel. Iran…