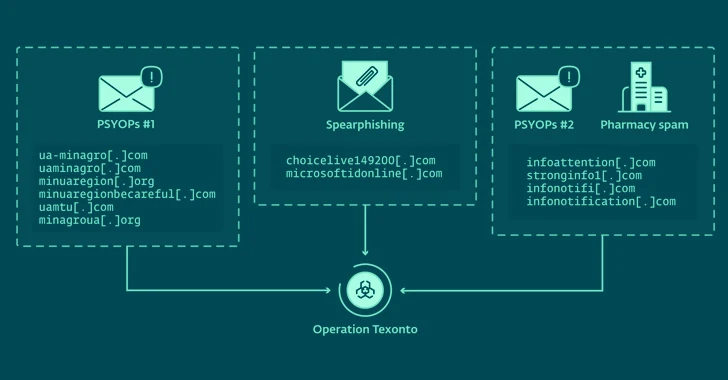
Russian Hackers Target Ukraine with Disinformation and Credential-Harvesting Attacks
[ad_1] Feb 21, 2024NewsroomPhishing Attack / Information Warfare Cybersecurity researchers have unearthed a new influence operation targeting Ukraine that leverages spam emails to propagate war-related disinformation. The activity has been linked to Russia-aligned threat actors by Slovak cybersecurity company ESET, which also identified a spear-phishing campaign aimed at a Ukrainian defense company in October 2023…