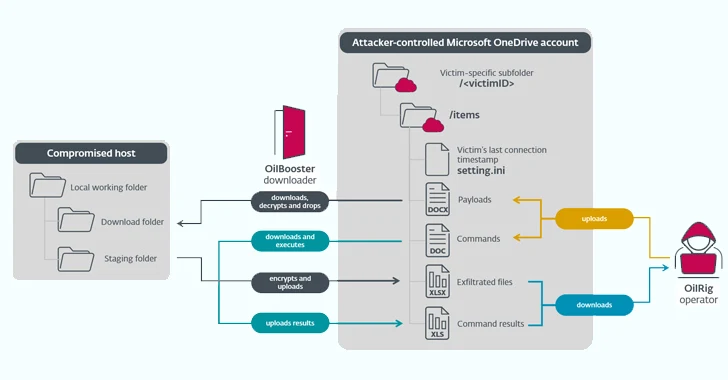
Reimagining Network Pentesting With Automation
[ad_1] Network penetration testing plays a crucial role in protecting businesses in the ever-evolving world of cybersecurity. Yet, business leaders and IT pros have misconceptions about this process, which impacts their security posture and decision-making. This blog acts as a quick guide on network penetration testing, explaining what it is, debunking common myths and reimagining…