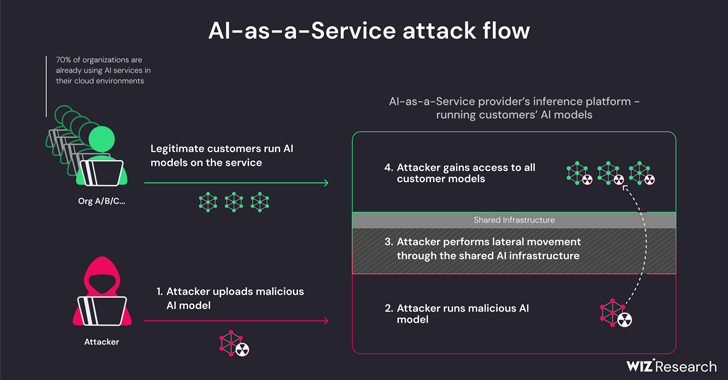
AI-as-a-Service Providers Vulnerable to PrivEsc and Cross-Tenant Attacks
[ad_1] Apr 05, 2024NewsroomArtificial Intelligence / Supply Chain Attack New research has found that artificial intelligence (AI)-as-a-service providers such as Hugging Face are susceptible to two critical risks that could allow threat actors to escalate privileges, gain cross-tenant access to other customers’ models, and even take over the continuous integration and continuous deployment (CI/CD) pipelines….



