A pro-Hamas threat actor known as Gaza Cyber Gang is targeting Palestinian entities using an updated version of a backdoor dubbed Pierogi.
The findings come from SentinelOne, which has given the malware the name Pierogi++ owing to the fact that it’s implemented in the C++ programming language unlike its Delphi- and Pascal-based predecessor.
“Recent Gaza Cybergang activities show consistent targeting of Palestinian entities, with no observed significant changes in dynamics since the start of the Israel-Hamas war,” security researcher Aleksandar Milenkoski said in a report shared with The Hacker News.
Gaza Cyber Gang, believed to be active since at least 2012, has a history of striking targets throughout the Middle East, particularly Israel and Palestine, often leveraging spear-phishing as a method of initial access.
From USER to ADMIN: Learn How Hackers Gain Full Control
Discover the secret tactics hackers use to become admins, how to detect and block it before it’s too late. Register for our webinar today.
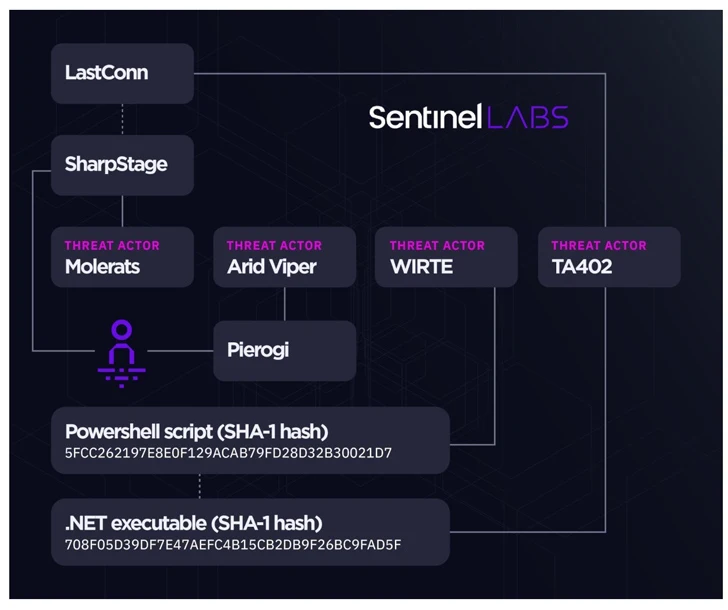
Some of the notable malware families in its arsenal include BarbWire, DropBook, LastConn, Molerat Loader, Micropsia, NimbleMamba, SharpStage, Spark, Pierogi, PoisonIvy, and XtremeRAT among others.
The threat actor is assessed to be a composite of several sub-groups that share overlapping victimology footprints and malware, such as Molerats, Arid Viper, and a cluster referred to as Operation Parliament by Kaspersky.
In recent months, the adversarial collective has been linked to a series of attacks that deliver improvised variants of its Micropsia and Arid Gopher implants as well as a new initial access downloader dubbed IronWind.
The latest set of intrusions mounted by Gaza Cyber Gang has been found to leverage Pierogi++ and Micropsia. The first recorded use of Pierogi++ goes back to late 2022.
Attack chains are characterized by the use of decoy documents written in Arabic or English and pertaining to matters of interest to Palestinians to deliver the backdoors.
Cybereason, which shed light on Pierogi in February 2020, described it as an implant that allows attackers to spy on targeted victims and that the “commands used to communicate with the [command-and-control] servers and other strings in the binary are written in Ukrainian.”
“The backdoor may have been obtained in underground communities rather than home-grown,” it assessed at the time.
Both Pierogi and Pierogi++ are equipped to take screenshots, execute commands, and download attacker-provided files. Another notable aspect is that the updated artifacts no longer feature any Ukrainian strings in the code.
SentinelOne’s investigation into Gaza Cyber Gang’s operations have also yielded tactical connections between two disparate campaigns referred to as Big Bang and Operation Bearded Barbie, in addition to reinforcing ties between the threat actor and WIRTE, as previously disclosed by Kaspersky in November 2021.
The sustained focus on Palestine notwithstanding, the discovery of Pierogi++ underscores that the group continues to refine and retool its malware to ensure successful compromise of targets and to maintain persistent access to their networks.
“The observed overlaps in targeting and malware similarities across the Gaza Cybergang sub-groups after 2018 suggests that the group has likely been undergoing a consolidation process,” Milenkoski said.
“This possibly includes the formation of an internal malware development and maintenance hub and/or streamlining supply from external vendors.”