New KV-Botnet Targeting Cisco, DrayTek, and Fortinet Devices for Stealthy Attacks
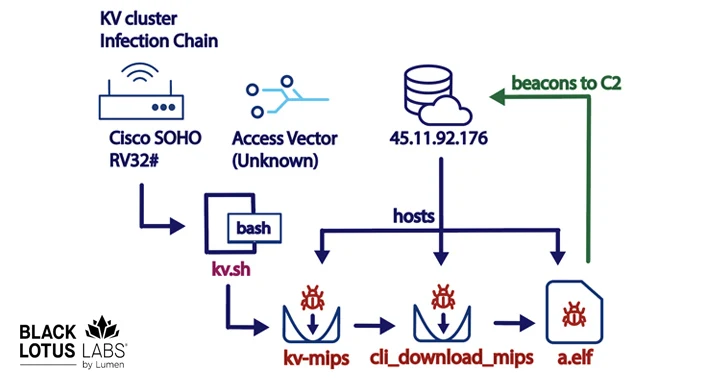
[ad_1] Dec 15, 2023NewsroomBotnet / Advanced Persistent Threat A new botnet consisting of firewalls and routers from Cisco, DrayTek, Fortinet, and NETGEAR is being used as a covert data transfer network for advanced persistent threat actors, including the China-linked threat actor called Volt Typhoon. Dubbed KV-botnet by the Black Lotus Labs team at Lumen Technologies,…














