Free Decryptor Released for Black Basta and Babuk’s Tortilla Ransomware Victims
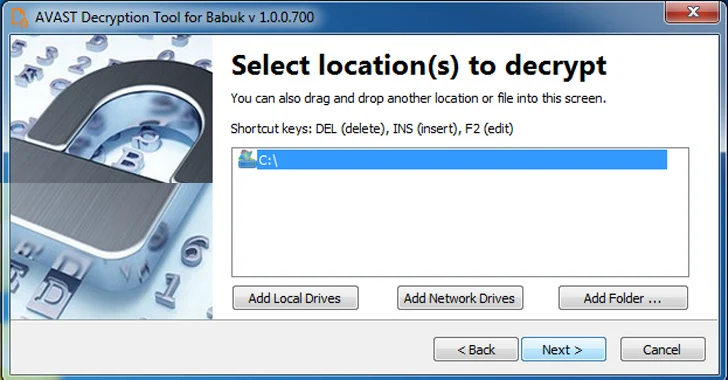
[ad_1] Jan 10, 2024NewsroomRansomware / Data Security A decryptor for the Tortilla variant of the Babuk ransomware has been released by Cisco Talos, allowing victims targeted by the malware to regain access to their files. The cybersecurity firm said the threat intelligence it shared with Dutch law enforcement authorities made it possible to arrest the…