[ad_1]
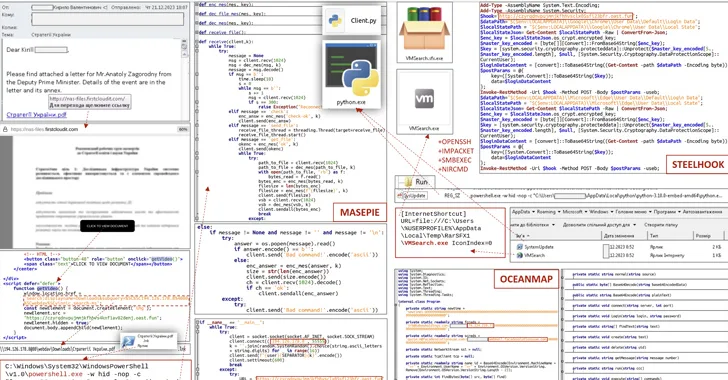
The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of a new phishing campaign orchestrated by the Russia-linked APT28 group to deploy previously undocumented malware such as OCEANMAP, MASEPIE, and STEELHOOK to harvest sensitive information.
The activity, which was detected by the agency between December 15 and 25, 2023, targets government entities with email messages urging recipients to click on a link to view a document.
From USER to ADMIN: Learn How Hackers Gain Full Control
Discover the secret tactics hackers use to become admins, how to detect and block it before it’s too late. Register for our webinar today.
However, to the contrary, the links redirect to malicious web resources that abuse JavaScript and the “search-ms:” URI protocol handler to drop a Windows shortcut file (LNK) that launches PowerShell commands to activate an infection chain for a new malware known as MASEPIE.
MASEPIE is a Python-based tool to download/upload files and execute commands, with communications with the command-and-control (C2) server taking place over an encrypted channel using the TCP protocol.
The attacks further pave the way for the deployment of additional malware, including a PowerShell script called STEELHOOK that’s capable of harvesting web browser data and exporting it to an actor-controlled server in Base64-encoded format.
Also delivered is a C#-based backdoor dubbed OCEANMAP that’s designed to execute commands using cmd.exe.
“The IMAP protocol is used as a control channel,” CERT-UA said, adding persistence is achieved by creating a URL file named “VMSearch.url” in the Windows Startup folder.
“Commands, in Base64-encoded form, are contained in the ‘Drafts’ of the corresponding email directories; each of the drafts contains the name of the computer, the name of the user and the version of the OS. The results of the commands are stored in the inbox directory.”
The agency further pointed out that reconnaissance and lateral movement activities are carried out within an hour of the initial compromise by taking advantage of tools like Impacket and SMBExec.
The disclosure comes weeks after IBM X-Force revealed APT28’s use of lures related to the ongoing Israel-Hamas war to facilitate the delivery of a custom backdoor called HeadLace.
In recent weeks, the prolific Kremlin-backed hacking group has also been attributed to the exploitation of a now-patched critical security flaw in its Outlook email service (CVE-2023-23397, CVSS score: 9.8) to gain unauthorized access to victims’ accounts within Exchange servers.
[ad_2]
Source link