[ad_1]
The remote access trojan (RAT) known as Remcos RAT has been found being propagated via webhards by disguising it as adult-themed games in South Korea.
WebHard, short for web hard drive, is a popular online file storage system used to upload, download, and share files in the country.
While webhards have been used in the past to deliver njRAT, UDP RAT, and DDoS botnet malware, the AhnLab Security Emergency Response Center’s (ASEC) latest analysis shows that the technique has been adopted to distribute Remcos RAT.
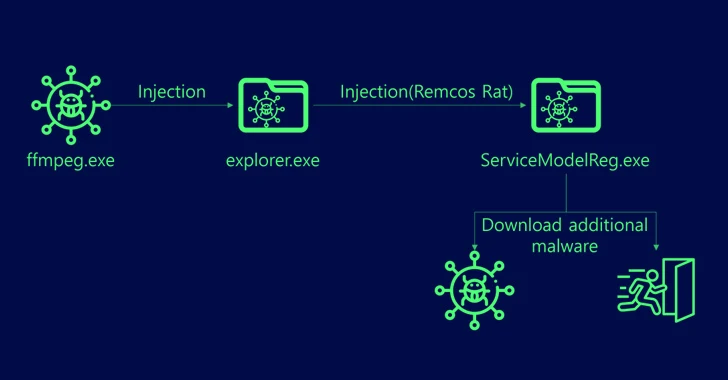
In these attacks, users are tricked into opening booby-trapped files by passing them off as adult games, which, when launched, execute malicious Visual Basic scripts in order to run an intermediate binary named “ffmpeg.exe.”
This results in the retrieval of Remcos RAT from an actor-controlled server.
A sophisticated RAT, Remcos (aka Remote Control and Surveillance) facilitates unauthorized remote control and surveillance of compromised hosts, enabling threat actors to exfiltrate sensitive data.
This malware, although originally marketed by Germany-based firm Breaking Security in 2016 as a bonafide remote administration tool, has metamorphosed into a potent weapon wielded by adversaries actors to infiltrate systems and establish unfettered control.
“Remcos RAT has evolved into a malicious tool employed by threat actors across various campaigns,” Cyfirma noted in an analysis in August 2023.
“The malware’s multifunctional capabilities, including keylogging, audio recording, screenshot capture, and more, highlight its potential to compromise user privacy, exfiltrate sensitive data, and manipulate systems. The RAT’s ability to disable User Account Control (UAC) and establish persistence further amplifies its potential impact.”
[ad_2]
Source link